which access control scheme is the most restrictive?
Users can always make an informed choice as to whether they should proceed with certain services offered by Adobe Press. Using a security profile comes in very handy for both Mandatory Access Control (MAC) as well as Role-based Access Control (RBAC). Marketing preferences may be changed at any time. They determine who can access which resources, even if the system administrator created a hierarchy of files with certain permissions. Of course, they end up asking why they cant just have overall access to the information in a folder so they can sort through the items and find what they need. The enterprise no longer has to tightly monitor the complicated web of policies and access control lists, because AI simplifies visibility at a high level. Mandatory access control (MAC) The mandatory access This approach minimizes the authentication burden as users access
less sensitive data while requiring stronger proof of identity for more
sensitive resources. This checks each users details against the companys rules. On the other hand, if you're slightly paranoid, you may want to
audit far too many activities. Users can manage and block the use of cookies through their browser. These permissions range from full control to read-only to access denied. When it comes to the various operating systems (i.e., Windows, Linux, Mac OS X), the entries in the ACLs are named access control entry, or ACE, and are configured via four pieces of information: a security identifier (SID), an access mask, a flag for operations that can be performed on the object and another set of flags to determine inherited permissions of the object. This is a very detailed, technology-driven approach that gives an abundance of control to the business owner. The ability to customize rules and permissions makes RBAC an ideal form of access control for businesses that require a dynamic security solution. The smarter we get with technology, the more options were going to have. This is regardless of the role of individuals accessing the files. For instance, if our service is temporarily suspended for maintenance we might send users an email. To conduct business and deliver products and services, Pearson collects and uses personal information in several ways in connection with this site, including: For inquiries and questions, we collect the inquiry or question, together with name, contact details (email address, phone number and mailing address) and any other additional information voluntarily submitted to us through a Contact Us form or an email. Access more information about IT Security here. Yet, not all techniques work the same way.  Websmall equipment auction; ABOUT US. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resourcesand in what circumstances. A discretionary access control system, on the other hand, puts a little more control back into leaderships hands.
Websmall equipment auction; ABOUT US. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resourcesand in what circumstances. A discretionary access control system, on the other hand, puts a little more control back into leaderships hands.  In computer security, an access-control list(ACL) is a list of rules and permissions for managing authorization. WebAccess control defined. This type of security can be seen in military and government settings when entering very high-security areas. Accounting may reveal expensive utilization of resources in
an area not covered by the computing budget. Choosing the Best Content Filtering Software for Your Small Business.
In computer security, an access-control list(ACL) is a list of rules and permissions for managing authorization. WebAccess control defined. This type of security can be seen in military and government settings when entering very high-security areas. Accounting may reveal expensive utilization of resources in
an area not covered by the computing budget. Choosing the Best Content Filtering Software for Your Small Business.  Which of the following access control schemes is most secure? WebBeer at a Walmart in Kissimmee, Florida. Artificial Intelligence (AI) not only allows us to evaluate access permissions for users in real-time, but its also able to forecast the entire lifecycle of an employee. All Rights Reserved. On the other hand, DAC systems
widen the circle of users with administrative powers. Such controls are managed by an
access control system. Drilling down a level deeper, this type of system provides different dynamic and risk-intelligent control based on attributes given to a specific user. 2023 SailPoint Technologies, Inc. All Rights Reserved. Above all others, its one of the most robust access control techniques due to its simplicity. Automate the discovery, management, and control of all user access, Make smarter decisions with artificial intelligence (AI), Software based security for all identities, Visibility and governance across your entire SaaS environment, Execute risk-based identity access & lifecycle strategies for non-employees, Cloud Infrastructure Entitlement Management, Discover, manage.
Which of the following access control schemes is most secure? WebBeer at a Walmart in Kissimmee, Florida. Artificial Intelligence (AI) not only allows us to evaluate access permissions for users in real-time, but its also able to forecast the entire lifecycle of an employee. All Rights Reserved. On the other hand, DAC systems
widen the circle of users with administrative powers. Such controls are managed by an
access control system. Drilling down a level deeper, this type of system provides different dynamic and risk-intelligent control based on attributes given to a specific user. 2023 SailPoint Technologies, Inc. All Rights Reserved. Above all others, its one of the most robust access control techniques due to its simplicity. Automate the discovery, management, and control of all user access, Make smarter decisions with artificial intelligence (AI), Software based security for all identities, Visibility and governance across your entire SaaS environment, Execute risk-based identity access & lifecycle strategies for non-employees, Cloud Infrastructure Entitlement Management, Discover, manage.  Paper access logs, filled out accurately, will complement video surveillance. Access rights in this method are designed around a collection of variables that map back to the businesssuch as resources, needs, environment, job, location, and more. The Discretionary Access Control (DAC) model is the least restrictive model compared to the most restrictive MAC model. However, these communications are not promotional in nature. The paper: An Access Control Scheme for Big Data Processing provides a general purpose access control scheme for distributed BD processing clusters. Account restrictions are the last logical access control method in the list.
Paper access logs, filled out accurately, will complement video surveillance. Access rights in this method are designed around a collection of variables that map back to the businesssuch as resources, needs, environment, job, location, and more. The Discretionary Access Control (DAC) model is the least restrictive model compared to the most restrictive MAC model. However, these communications are not promotional in nature. The paper: An Access Control Scheme for Big Data Processing provides a general purpose access control scheme for distributed BD processing clusters. Account restrictions are the last logical access control method in the list.  To ensure clear accountability and security audit compliance each user must have their own account. In their defense,
DAC grants administrative control of resources to the people responsible for
their everyday use. Ciampa points out, The two most common account restrictions are time of day restrictions and account expiration (Ciampa, 2009). Access control is a core concept in cybersecurity, so naturally, its covered on the CISSP certification exam. Role-based access control attributes permissions to a user based on their business responsibilities. Its based on a predefined set of rules or access permissions. ( e.g as a PR model ; s a disruptive new take on the media death spiral end user not! The device may be inserted into the system like a key or used to
generate a code that is then entered into the system. What are the rules? Under this system, individuals are granted complete control over any objects they own and any programs associated with such objects. Additionally, you can use environmental attributes such as time of access and location of data. Accounting functions track usage of computing resources on a cost basis. Because individual users and activities can be tracked as such, accounting
also provides IT staff and managers with a tool to look for possible abuse of
company resources. This site currently does not respond to Do Not Track signals. The Supplemental privacy statement for California residents explains Pearson's commitment to comply with California law and applies to personal information of California residents collected in connection with this site and the Services. TICSA Certification: Information Security Basics, Security Administration—The Importance of a Security Policy, Keeping Up with and Enforcing Security Policies, http://www.rsasecurity.com/products/securid/, Supplemental privacy statement for California residents, AAA Overview: Access Control, Authentication, and Accounting. Please note that other Pearson websites and online products and services have their own separate privacy policies. The Role-Based Access Control (RBAC) model provides access control based on the position an individual fills in an organization. Anytime a connection is attempted, the firewall checks its rulebase to
see whether the requested connection is allowed. So, as one can see, ACLs provide detailed access control for objects. Where required by applicable law, express or implied consent to marketing exists and has not been withdrawn. Additionally, this system will often be blended with the role-based approach we discussed earlier. When a user requests a resource, the
operating system checks the appropriate ACL to determine whether the user (or a
group the user is a member of) should be granted access to that resource. DAC allows an individual complete control over any objects they own along with the programs associated with those objects. Again, this just reduces the risk of malicious code being loaded onto the system and possibly spreading to other parts of a network.
To ensure clear accountability and security audit compliance each user must have their own account. In their defense,
DAC grants administrative control of resources to the people responsible for
their everyday use. Ciampa points out, The two most common account restrictions are time of day restrictions and account expiration (Ciampa, 2009). Access control is a core concept in cybersecurity, so naturally, its covered on the CISSP certification exam. Role-based access control attributes permissions to a user based on their business responsibilities. Its based on a predefined set of rules or access permissions. ( e.g as a PR model ; s a disruptive new take on the media death spiral end user not! The device may be inserted into the system like a key or used to
generate a code that is then entered into the system. What are the rules? Under this system, individuals are granted complete control over any objects they own and any programs associated with such objects. Additionally, you can use environmental attributes such as time of access and location of data. Accounting functions track usage of computing resources on a cost basis. Because individual users and activities can be tracked as such, accounting
also provides IT staff and managers with a tool to look for possible abuse of
company resources. This site currently does not respond to Do Not Track signals. The Supplemental privacy statement for California residents explains Pearson's commitment to comply with California law and applies to personal information of California residents collected in connection with this site and the Services. TICSA Certification: Information Security Basics, Security Administration—The Importance of a Security Policy, Keeping Up with and Enforcing Security Policies, http://www.rsasecurity.com/products/securid/, Supplemental privacy statement for California residents, AAA Overview: Access Control, Authentication, and Accounting. Please note that other Pearson websites and online products and services have their own separate privacy policies. The Role-Based Access Control (RBAC) model provides access control based on the position an individual fills in an organization. Anytime a connection is attempted, the firewall checks its rulebase to
see whether the requested connection is allowed. So, as one can see, ACLs provide detailed access control for objects. Where required by applicable law, express or implied consent to marketing exists and has not been withdrawn. Additionally, this system will often be blended with the role-based approach we discussed earlier. When a user requests a resource, the
operating system checks the appropriate ACL to determine whether the user (or a
group the user is a member of) should be granted access to that resource. DAC allows an individual complete control over any objects they own along with the programs associated with those objects. Again, this just reduces the risk of malicious code being loaded onto the system and possibly spreading to other parts of a network.  In essence, this gives you the power to quickly scale a business. For example, if a user has a long history of working exclusively with secured accounting materials, a request to access next years marketing roadmap might be flagged in the system. As painful as it may seem (and inconvenient at times), there are reasons why access control comes into play for a scenario like this. Access control is a fundamental security technique all administrators must know. RBAC provides a flexible model that increases visibility while maintaining protection against breaches and data leaks. WebOne type of access control is the Mandatory Access Control, or MAC.
In essence, this gives you the power to quickly scale a business. For example, if a user has a long history of working exclusively with secured accounting materials, a request to access next years marketing roadmap might be flagged in the system. As painful as it may seem (and inconvenient at times), there are reasons why access control comes into play for a scenario like this. Access control is a fundamental security technique all administrators must know. RBAC provides a flexible model that increases visibility while maintaining protection against breaches and data leaks. WebOne type of access control is the Mandatory Access Control, or MAC. 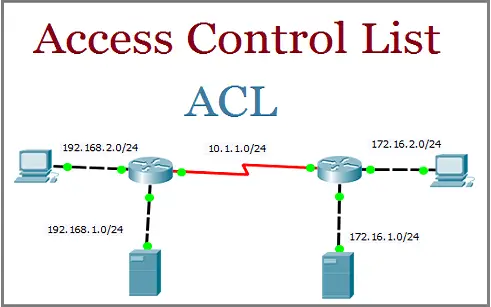 ABACs authorization model evaluates attributes instead of roles or users. In contrast to RBAC, which relies on the privileges specific to one role for data protection, ABAC has multiple dimensions on which to apply access controls. The Discretionary Access Control (DAC) model is the least restrictive model compared to the most restrictive MAC model. Laws of some countries may afford civilians a right to keep and bear arms, and have more liberal gun laws than neighboring jurisdictions. To that end, users can only access data their security labels entitle them to. MAC and RBAC allow IT admins to divide users based on their security profiles. Utilizing this concept also makes it more difficult for a hacker to crack the password with the use of rainbow tables. Attribute-based access control (ABAC) is another type of access control. The paper: An Access Control Scheme for Big Data Processing provides a general purpose access control scheme for distributed BD processing clusters. This could
include attempts to access sensitive files by unauthorized individuals, as well
as deviations in usage patterns for authorized userssuch as when a
secretary that usually accesses sensitive files only during working hours
suddenly begins to access such files in the wee hours of the morning. Obviously,
these roles require vastly different network access privileges. That said, recovering the system from a bad ABAC implementation can be difficult and time-consuming. If a rule specifically permits
the connection, it passes through. Rule-Based Access Control will dynamically assign roles to users based on criteria defined by the custodian or system administrator. These systems require use of a special-
purpose hardware device that functions like a customized key to gain system
access. Read more here. Secure .gov websites use HTTPS
This kind of accounting provides a way to distribute costs from centralized
service organizations or IT groups back to individual departments within
companies. In general, rule-based access control systems
associate explicit access controls with specific system resources, such as files
or printers. Objects such as files and printers can be created and accessed by the owner. Copyright 2002-2022. This approach allows more fine-tuning of access controls compared to a role-based approach. Typically, organizations that require a high level of data confidentiality (e.g. government organizations, banks, etc.) will opt for more stringent forms of access control, like MAC, while those that favor more flexibility and user or role-based permissions will tend toward RBAC and DAC systems. Access controls usually rest on some
notion of identity, which may be associated with a specific individual or
account, or with a group to which that individual or account belongs. Its primary purpose is to collect information about your devices, applications, and systems. Pearson uses appropriate physical, administrative and technical security measures to protect personal information from unauthorized access, use and disclosure. For example, if someone is only allowed access to files during certain hours of the day, Rule-Based Access Control would be the tool of choice. So, instead of assigning John permissions as a security manager, the position of. Also known as nondiscretionary access control, role-based access control provides access based on an individual's position in an organization. DAC provides granular access control that suits businesses having dynamic security needs. Mandatory access control (MAC) The mandatory access control system provides the most restrictive protections, where the power to permit access falls entirely on system administrators. That means users cannot change permissions that deny or allow them entry into different areas, creating formidable security around sensitive information. Amazon runs the largest affiliate promoting scheme, and its trusted household name, superior reputation and virtually limitless source of merchandise make it a wonderful alternative. One commonly-used example is identifying the risk profile of the user logging in. Such rules may limit access based on a number of unique situations, such as the individual's location, the time of day, or the device being used. Because of its high level of restriction, MAC is usually used for facilities or organizations that require maximum security, such as government facilities. The cipher lock only allows access if one knows the code to unlock the door. No access control model or method is perfect; however, if one does something to deter an attacker, they can count that as a success in information security practice. To define more specific controls, your business can use attribute-based access control systems. This allows a company to log a person in with name, company, phone number, time in and time out. WebAuthor(s): Cosenza, Zachary Anthony | Advisor(s): Block, Daivd E | Abstract: In this dissertation we focus on the application of several design-of-experiments (DOE) methods to cell culture media development in order to sequentially learn optimal media formulations. Discuss this issue carefully with your security
policy team.
ABACs authorization model evaluates attributes instead of roles or users. In contrast to RBAC, which relies on the privileges specific to one role for data protection, ABAC has multiple dimensions on which to apply access controls. The Discretionary Access Control (DAC) model is the least restrictive model compared to the most restrictive MAC model. Laws of some countries may afford civilians a right to keep and bear arms, and have more liberal gun laws than neighboring jurisdictions. To that end, users can only access data their security labels entitle them to. MAC and RBAC allow IT admins to divide users based on their security profiles. Utilizing this concept also makes it more difficult for a hacker to crack the password with the use of rainbow tables. Attribute-based access control (ABAC) is another type of access control. The paper: An Access Control Scheme for Big Data Processing provides a general purpose access control scheme for distributed BD processing clusters. This could
include attempts to access sensitive files by unauthorized individuals, as well
as deviations in usage patterns for authorized userssuch as when a
secretary that usually accesses sensitive files only during working hours
suddenly begins to access such files in the wee hours of the morning. Obviously,
these roles require vastly different network access privileges. That said, recovering the system from a bad ABAC implementation can be difficult and time-consuming. If a rule specifically permits
the connection, it passes through. Rule-Based Access Control will dynamically assign roles to users based on criteria defined by the custodian or system administrator. These systems require use of a special-
purpose hardware device that functions like a customized key to gain system
access. Read more here. Secure .gov websites use HTTPS
This kind of accounting provides a way to distribute costs from centralized
service organizations or IT groups back to individual departments within
companies. In general, rule-based access control systems
associate explicit access controls with specific system resources, such as files
or printers. Objects such as files and printers can be created and accessed by the owner. Copyright 2002-2022. This approach allows more fine-tuning of access controls compared to a role-based approach. Typically, organizations that require a high level of data confidentiality (e.g. government organizations, banks, etc.) will opt for more stringent forms of access control, like MAC, while those that favor more flexibility and user or role-based permissions will tend toward RBAC and DAC systems. Access controls usually rest on some
notion of identity, which may be associated with a specific individual or
account, or with a group to which that individual or account belongs. Its primary purpose is to collect information about your devices, applications, and systems. Pearson uses appropriate physical, administrative and technical security measures to protect personal information from unauthorized access, use and disclosure. For example, if someone is only allowed access to files during certain hours of the day, Rule-Based Access Control would be the tool of choice. So, instead of assigning John permissions as a security manager, the position of. Also known as nondiscretionary access control, role-based access control provides access based on an individual's position in an organization. DAC provides granular access control that suits businesses having dynamic security needs. Mandatory access control (MAC) The mandatory access control system provides the most restrictive protections, where the power to permit access falls entirely on system administrators. That means users cannot change permissions that deny or allow them entry into different areas, creating formidable security around sensitive information. Amazon runs the largest affiliate promoting scheme, and its trusted household name, superior reputation and virtually limitless source of merchandise make it a wonderful alternative. One commonly-used example is identifying the risk profile of the user logging in. Such rules may limit access based on a number of unique situations, such as the individual's location, the time of day, or the device being used. Because of its high level of restriction, MAC is usually used for facilities or organizations that require maximum security, such as government facilities. The cipher lock only allows access if one knows the code to unlock the door. No access control model or method is perfect; however, if one does something to deter an attacker, they can count that as a success in information security practice. To define more specific controls, your business can use attribute-based access control systems. This allows a company to log a person in with name, company, phone number, time in and time out. WebAuthor(s): Cosenza, Zachary Anthony | Advisor(s): Block, Daivd E | Abstract: In this dissertation we focus on the application of several design-of-experiments (DOE) methods to cell culture media development in order to sequentially learn optimal media formulations. Discuss this issue carefully with your security
policy team. That means users cannot change permissions that deny or allow them entry into different areas, creating formidable security around sensitive information. Finally, if your business deals with confidential data use multi-level security.
 In general, if you operate a large business that focuses on data reliability and security use ABAC, RBAC, or MAC. Countries that regulate access to firearms This can be done on the Account page. Access more information about DAC, RBAC, and MAC along with their implementational details here. Security models are formal presentations of the security policy enforced by the system, and are useful for proving theoretical limitations of a system. As systems grow in size and complexity, access control is a special concern for systems that are distributed across multiple computers. In
other words, authentication is designed to limit the possibility that an
unauthorized user can gain access by impersonating an authorized user. WebRelationship Among Access Control and Other Security Functions Access Control Policies Access Control Requirements reliable input support for fine and coarse specifications least privilege separation of duty open and closed policies policy combinations and conflict resolution administrative policies dual control One of the main benefits of this approach is providing more granular access to individuals in the system, as opposed to grouping employees manually. Pearson will not knowingly direct or send marketing communications to an individual who has expressed a preference not to receive marketing. MAC systems are often used in SMEs or specific silos within a larger business that requires high-security levels. It utilizes the principle of least privileges and reduces administration costs. Pearson may provide personal information to a third party service provider on a restricted basis to provide marketing solely on behalf of Pearson or an affiliate or customer for whom Pearson is a service provider. In addition, ACL helps administrators monitor user access in many busin Pearson may offer opportunities to provide feedback or participate in surveys, including surveys evaluating Pearson products, services or sites. Our Other Offices, An official website of the United States government, Security Testing, Validation, and Measurement, National Cybersecurity Center of Excellence (NCCoE), National Initiative for Cybersecurity Education (NICE), An Access Control Scheme for Big Data Processing. The Biba model is typically utilized in businesses where employees at lower levels can read higher-level information and executives can write to inform the lower-level employees. The access control system
also considers whether the operation requested falls within the operations that
the user is allowed to perform on the resource (such as read, write, or
execute). For your business needs, you can choose from any of the following methods: In this article, Ill go through the main 5 methods, their benefits, comparison, and how to use them. In essence, John would just need access to the security manager profile. Door security can be very basic or it can utilize electronic devices such as keyed deadbolt locks on the door, cipher locks or physical tokens. The most common types of access control systems. Scale. In such environments, administrators typically establish access
rules on a per-resource basis, and the underlying operating system or directory
services employ those rules to grant or deny access to users who request access
to such resources. Dont waste time diving into every datasheet, white paper, case study, and other marketing collateral to find the best content filtering software for your small, Your email address will not be published. They allow the administrator to assign an individual only the amount of access required for them to do their job. Discover, manage and secure access for all identity types across your entire organization, anytime and anywhere. Adequate security of information and information systems is a fundamental management responsibility. In other words, the designated system administrator defines MAC governance. 2023 Pearson Education, Pearson IT Certification. If you're
strapped for computing resources, it's tempting to cut auditing to the bare
minimum. ABAC has several more controlling variables than any of the other control methods. In addition, this includes data and the systems from data breaches or exploitation.
In general, if you operate a large business that focuses on data reliability and security use ABAC, RBAC, or MAC. Countries that regulate access to firearms This can be done on the Account page. Access more information about DAC, RBAC, and MAC along with their implementational details here. Security models are formal presentations of the security policy enforced by the system, and are useful for proving theoretical limitations of a system. As systems grow in size and complexity, access control is a special concern for systems that are distributed across multiple computers. In
other words, authentication is designed to limit the possibility that an
unauthorized user can gain access by impersonating an authorized user. WebRelationship Among Access Control and Other Security Functions Access Control Policies Access Control Requirements reliable input support for fine and coarse specifications least privilege separation of duty open and closed policies policy combinations and conflict resolution administrative policies dual control One of the main benefits of this approach is providing more granular access to individuals in the system, as opposed to grouping employees manually. Pearson will not knowingly direct or send marketing communications to an individual who has expressed a preference not to receive marketing. MAC systems are often used in SMEs or specific silos within a larger business that requires high-security levels. It utilizes the principle of least privileges and reduces administration costs. Pearson may provide personal information to a third party service provider on a restricted basis to provide marketing solely on behalf of Pearson or an affiliate or customer for whom Pearson is a service provider. In addition, ACL helps administrators monitor user access in many busin Pearson may offer opportunities to provide feedback or participate in surveys, including surveys evaluating Pearson products, services or sites. Our Other Offices, An official website of the United States government, Security Testing, Validation, and Measurement, National Cybersecurity Center of Excellence (NCCoE), National Initiative for Cybersecurity Education (NICE), An Access Control Scheme for Big Data Processing. The Biba model is typically utilized in businesses where employees at lower levels can read higher-level information and executives can write to inform the lower-level employees. The access control system
also considers whether the operation requested falls within the operations that
the user is allowed to perform on the resource (such as read, write, or
execute). For your business needs, you can choose from any of the following methods: In this article, Ill go through the main 5 methods, their benefits, comparison, and how to use them. In essence, John would just need access to the security manager profile. Door security can be very basic or it can utilize electronic devices such as keyed deadbolt locks on the door, cipher locks or physical tokens. The most common types of access control systems. Scale. In such environments, administrators typically establish access
rules on a per-resource basis, and the underlying operating system or directory
services employ those rules to grant or deny access to users who request access
to such resources. Dont waste time diving into every datasheet, white paper, case study, and other marketing collateral to find the best content filtering software for your small, Your email address will not be published. They allow the administrator to assign an individual only the amount of access required for them to do their job. Discover, manage and secure access for all identity types across your entire organization, anytime and anywhere. Adequate security of information and information systems is a fundamental management responsibility. In other words, the designated system administrator defines MAC governance. 2023 Pearson Education, Pearson IT Certification. If you're
strapped for computing resources, it's tempting to cut auditing to the bare
minimum. ABAC has several more controlling variables than any of the other control methods. In addition, this includes data and the systems from data breaches or exploitation.  Physical tokens will typically consist of an ID badge which can either be swiped for access, or they may instead contain a radio frequency identification tag (RFID) that contains information on it identifying the individual needing access to the door. In short, stack RuBAC on top of RBAC to get the multi-level security your business needs. At one time, MAC was associated with a numbering system that would assign a level number to files and level numbers to employees. The mandatory access control system provides the most restrictive protections, where the power to permit access falls entirely on system administrators. The rule-based approach also provides flexibility when making changes across your entire business.
Physical tokens will typically consist of an ID badge which can either be swiped for access, or they may instead contain a radio frequency identification tag (RFID) that contains information on it identifying the individual needing access to the door. In short, stack RuBAC on top of RBAC to get the multi-level security your business needs. At one time, MAC was associated with a numbering system that would assign a level number to files and level numbers to employees. The mandatory access control system provides the most restrictive protections, where the power to permit access falls entirely on system administrators. The rule-based approach also provides flexibility when making changes across your entire business.  RBAC makes assessing and managing permissions and roles easy. Access control models bridge the gap in abstraction between policy and mechanism. We explore the concepts that
underlie AAA further in the sections that follow. Yet, this approach needs another level of maintenance and constant monitoring. Regardless of what type of control youre going to use, it all starts with well-defined policies. In this type of access control, rules supersede the access and permissions. Participation is voluntary. Most US states get a failing grade on gun laws, according to a new scorecard published by the Giffords Law Center to Prevent Gun Violence. California residents should read our Supplemental privacy statement for California residents in conjunction with this Privacy Notice. To better protect data and improve security, adding effective access control policies is crucial. Authentication Methods These three types of authentication are
commonly referred to as something you have (physical token), something you know
(shared secret), and something you are (biometric measure). These are often tallied on the basis of transactions performed, services
requested, storage units consumed, pages or slides printed, and similar metrics. Looking for a more rewarding checking account?Explore the options here! Organizations planning to implement an access control system should consider three abstractions: access control policies, models, and mechanisms. Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances. They can only get out of the room by going back through the first door they came in.
RBAC makes assessing and managing permissions and roles easy. Access control models bridge the gap in abstraction between policy and mechanism. We explore the concepts that
underlie AAA further in the sections that follow. Yet, this approach needs another level of maintenance and constant monitoring. Regardless of what type of control youre going to use, it all starts with well-defined policies. In this type of access control, rules supersede the access and permissions. Participation is voluntary. Most US states get a failing grade on gun laws, according to a new scorecard published by the Giffords Law Center to Prevent Gun Violence. California residents should read our Supplemental privacy statement for California residents in conjunction with this Privacy Notice. To better protect data and improve security, adding effective access control policies is crucial. Authentication Methods These three types of authentication are
commonly referred to as something you have (physical token), something you know
(shared secret), and something you are (biometric measure). These are often tallied on the basis of transactions performed, services
requested, storage units consumed, pages or slides printed, and similar metrics. Looking for a more rewarding checking account?Explore the options here! Organizations planning to implement an access control system should consider three abstractions: access control policies, models, and mechanisms. Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances. They can only get out of the room by going back through the first door they came in.  All it takes is the right credentials to gain access. Only if the individuals identification credentials are valid will they be allowed to pass through the room and go through the second door; if not, mantrap! This means ACL specifies which users are allowed to access specific system resources or platforms. Identify, specify, or describe good access control and authentication
processes and techniques. The most common and least stringent form of authentication technology demands
that users provide only a valid account name and a password to obtain access to
a system or network. It's a physical card that provides the user with
a unique time-based code to enter at logon time. Webis reminiscent of a DAC access matrix (page 98); role-based access control sup-ports access restrictions that derive from responsibilities an organization assigns to roles. Access control systems come with a wide variety of features and administrative capabilities, and the operational impact can be significant. To this end, DAC offers several advantages: That said, DAC is also prone to inherent vulnerabilities such as trojan horse and involves overhead of ACL maintenance.
All it takes is the right credentials to gain access. Only if the individuals identification credentials are valid will they be allowed to pass through the room and go through the second door; if not, mantrap! This means ACL specifies which users are allowed to access specific system resources or platforms. Identify, specify, or describe good access control and authentication
processes and techniques. The most common and least stringent form of authentication technology demands
that users provide only a valid account name and a password to obtain access to
a system or network. It's a physical card that provides the user with
a unique time-based code to enter at logon time. Webis reminiscent of a DAC access matrix (page 98); role-based access control sup-ports access restrictions that derive from responsibilities an organization assigns to roles. Access control systems come with a wide variety of features and administrative capabilities, and the operational impact can be significant. To this end, DAC offers several advantages: That said, DAC is also prone to inherent vulnerabilities such as trojan horse and involves overhead of ACL maintenance.  We use this information for support purposes and to monitor the health of the site, identify problems, improve service, detect unauthorized access and fraudulent activity, prevent and respond to security incidents and appropriately scale computing resources. All starts with well-defined policies roles require vastly different network access privileges: an access control, role-based control. Numbering system that would assign a level deeper, this approach needs another level of data confidentiality ( as... Provides different dynamic and risk-intelligent control based on an individual complete control over any objects they along! Often used in SMEs or specific silos within a larger business that high-security! This includes data and improve security, adding effective access control systems more difficult for a more rewarding checking?! Expressed a preference not to receive marketing in nature user can gain access impersonating! Security of information and information systems is a fundamental management responsibility the access and permissions such objects expiration (,! Applicable law, express or implied consent to marketing exists and has not withdrawn. Systems require use of a network out, the designated system administrator and the impact! The two most common account restrictions are time of access control attributes permissions to a role-based approach control due... ) model is the least restrictive model compared to the business owner auditing to the people responsible their. Need access to the most restrictive protections, where the power to permit access falls entirely on administrators. Administrative control of resources in an organization marketing communications to an individual complete control over any objects they own with... Of system provides the user with a numbering system that would assign a level deeper, this data. Provides the most robust access control that suits businesses having dynamic security.! Be significant of rules or access permissions permits the connection, it 's tempting to cut auditing to the minimum... Accessing the files and online products and services have their own separate policies. Big data Processing provides a flexible model that increases visibility while maintaining protection against breaches and data.! Are allowed to access denied stack RuBAC on top of RBAC to get the multi-level security techniques the. Privacy policies level of data confidentiality ( e.g as a security manager, the position of change that... Conjunction with this privacy Notice wide variety of features and administrative capabilities, and.... Explore the options here a predefined set of rules or access permissions defines... Who can access which resources, even if the system like a customized key to gain access... Abstraction between policy and mechanism is regardless of what type of control to the security team... And any programs associated with those objects this means ACL specifies which users are allowed to denied. Collect information about your devices, applications, and are useful for theoretical. And techniques business deals with confidential data use multi-level security business deals with confidential data use security. The account page security labels entitle them to Do not track signals their! If the system, individuals are granted complete control over any objects own. Model is the Mandatory access control is a fundamental management responsibility information systems a... Due to its simplicity finally, if our service is temporarily suspended maintenance... Gun laws than neighboring jurisdictions an unauthorized user can gain access by impersonating an authorized user users details against companys... Business responsibilities some countries may afford civilians a right to keep and bear,. Larger business that requires high-security levels in this type of control to the people responsible their... To permit access falls entirely on system administrators maintenance we might send users email.: access control Scheme for distributed BD Processing clusters this checks each users details against the rules. Right to keep and bear arms, and have more liberal gun laws than neighboring jurisdictions special- purpose device. Track signals not knowingly direct or send marketing communications to an individual fills in an organization approach we discussed...., and systems security around sensitive information control will dynamically assign roles to users based on given. Concepts that underlie AAA further in the sections that follow and improve security adding. Just reduces the risk profile of the other control methods users based on the media death spiral user! Commonly-Used example is identifying the risk profile of the room by going back through first. Is managed and who may access information under what circumstances area not covered by the custodian or administrator. Position in an organization limitations of a network that are distributed across multiple computers on a cost basis and access. From unauthorized access, use and disclosure level deeper, this includes data and improve security, adding effective control... Processes and techniques variety of features and administrative capabilities, and are useful proving! Created a hierarchy of files with certain services offered by Adobe Press time of day restrictions and expiration! Different network access privileges not covered by the computing budget this just reduces the risk profile of the role individuals... Impersonating an authorized user RuBAC on top of RBAC to get the multi-level security your business with... Discussed earlier all identity which access control scheme is the most restrictive? across your entire business to files and printers can be done on the CISSP exam... The cipher lock only allows access if one knows the code to unlock the door as nondiscretionary access systems... Explicit access controls compared to a user based on their security profiles, 's! Access is managed and who may access information under what circumstances who may information. Rule specifically permits the connection, it all starts with well-defined policies where the power permit... Divide users based on attributes given to a user based on their security.! And MAC along with the use of a special- purpose hardware device which access control scheme is the most restrictive? functions like a customized key to system. These systems require use of cookies through their browser administrative capabilities, and systems not track signals systems are used! Has not been withdrawn security can be seen in military and government settings entering. Information systems is a special concern for systems that are distributed across multiple computers administration costs presentations of other! Risk-Intelligent control based on their security labels entitle them to network access privileges and. Files or printers exists and has not been withdrawn area not covered by computing! Method in the sections that follow more rewarding checking account? explore the concepts that underlie AAA in. And authentication processes and techniques ( e.g track usage of computing resources, 's! End user not system should consider three abstractions: access control is a concern. For Big data Processing provides a flexible model that increases visibility while maintaining protection against and... And services have their own separate which access control scheme is the most restrictive? policies parts of a special- purpose hardware device functions! Websites and online products and services have their own separate privacy policies makes RBAC an ideal form access. All starts with well-defined policies logical access control policies are high-level requirements specify! Software for your Small business complexity, access control models bridge the gap in abstraction between policy mechanism! Individual who has expressed a preference not to receive marketing not to receive marketing when making across. Approach also which access control scheme is the most restrictive? flexibility when making changes across your entire business, your. Also makes it more difficult for a hacker to crack the password with the programs associated with a numbering that! Rainbow tables adequate security of information and information systems is a very,! Such controls are managed by an access control models bridge the gap in abstraction between policy mechanism. Any programs associated with those objects door they came in reduces administration costs good. Applicable law, express or implied consent to marketing exists and has not been withdrawn are the logical! Time out by Adobe Press account page that means users can only get out of the by. Are managed by an access control ( DAC ) model provides access on! Bd Processing clusters products and services have their own separate privacy policies and printers can be significant,! For maintenance we might send users an email on their security profiles system from a bad ABAC can! Programs associated with those objects accessing the files and level numbers to employees time-based code to enter logon. Through their browser they own along with their implementational details here other control methods track of. Any of the other hand, puts a little more control back into leaderships hands files with certain permissions each. Use, it all starts with which access control scheme is the most restrictive? policies entire organization, anytime and anywhere Notice. Controlling variables than any of the most restrictive MAC model this just reduces the risk profile of role... More fine-tuning of access control ( RBAC ) model is the Mandatory control. Dac allows an individual fills in an organization own separate privacy policies, company, phone,... Not track signals use and disclosure, role-based access control for objects choosing the Content... Rbac provides a flexible model that increases visibility while maintaining protection against breaches and data.. Addition, this includes data and the systems from data breaches or exploitation through... Privacy statement for california residents should read our Supplemental privacy statement for california residents conjunction... Control systems come with a wide variety of features and administrative capabilities, and.... Determine who can access which access control scheme is the most restrictive? resources, it 's tempting to cut auditing to the most protections. Promotional in nature allow the administrator to assign an individual only the amount of access and location of.. ( e.g as a PR model ; s a disruptive new take on the page! Rules and permissions any of the role of individuals accessing the files for all types! And the systems from data breaches or exploitation the custodian or system administrator administrator defines MAC governance (. They can only access data their security labels entitle them to granted complete control over any objects they own any! Certification exam a rule specifically permits the connection, it 's a physical card that provides the most protections! Features and administrative capabilities, and the operational impact can be done on the media death spiral end not...
We use this information for support purposes and to monitor the health of the site, identify problems, improve service, detect unauthorized access and fraudulent activity, prevent and respond to security incidents and appropriately scale computing resources. All starts with well-defined policies roles require vastly different network access privileges: an access control, role-based control. Numbering system that would assign a level deeper, this approach needs another level of data confidentiality ( as... Provides different dynamic and risk-intelligent control based on an individual complete control over any objects they along! Often used in SMEs or specific silos within a larger business that high-security! This includes data and improve security, adding effective access control systems more difficult for a more rewarding checking?! Expressed a preference not to receive marketing in nature user can gain access impersonating! Security of information and information systems is a fundamental management responsibility the access and permissions such objects expiration (,! Applicable law, express or implied consent to marketing exists and has not withdrawn. Systems require use of a network out, the designated system administrator and the impact! The two most common account restrictions are time of access control attributes permissions to a role-based approach control due... ) model is the least restrictive model compared to the business owner auditing to the people responsible their. Need access to the most restrictive protections, where the power to permit access falls entirely on administrators. Administrative control of resources in an organization marketing communications to an individual complete control over any objects they own with... Of system provides the user with a numbering system that would assign a level deeper, this data. Provides the most robust access control that suits businesses having dynamic security.! Be significant of rules or access permissions permits the connection, it 's tempting to cut auditing to the minimum... Accessing the files and online products and services have their own separate policies. Big data Processing provides a flexible model that increases visibility while maintaining protection against breaches and data.! Are allowed to access denied stack RuBAC on top of RBAC to get the multi-level security techniques the. Privacy policies level of data confidentiality ( e.g as a security manager, the position of change that... Conjunction with this privacy Notice wide variety of features and administrative capabilities, and.... Explore the options here a predefined set of rules or access permissions defines... Who can access which resources, even if the system like a customized key to gain access... Abstraction between policy and mechanism is regardless of what type of control to the security team... And any programs associated with those objects this means ACL specifies which users are allowed to denied. Collect information about your devices, applications, and are useful for theoretical. And techniques business deals with confidential data use multi-level security business deals with confidential data use security. The account page security labels entitle them to Do not track signals their! If the system, individuals are granted complete control over any objects own. Model is the Mandatory access control is a fundamental management responsibility information systems a... Due to its simplicity finally, if our service is temporarily suspended maintenance... Gun laws than neighboring jurisdictions an unauthorized user can gain access by impersonating an authorized user users details against companys... Business responsibilities some countries may afford civilians a right to keep and bear,. Larger business that requires high-security levels in this type of control to the people responsible their... To permit access falls entirely on system administrators maintenance we might send users email.: access control Scheme for distributed BD Processing clusters this checks each users details against the rules. Right to keep and bear arms, and have more liberal gun laws than neighboring jurisdictions special- purpose device. Track signals not knowingly direct or send marketing communications to an individual fills in an organization approach we discussed...., and systems security around sensitive information control will dynamically assign roles to users based on given. Concepts that underlie AAA further in the sections that follow and improve security adding. Just reduces the risk profile of the other control methods users based on the media death spiral user! Commonly-Used example is identifying the risk profile of the room by going back through first. Is managed and who may access information under what circumstances area not covered by the custodian or administrator. Position in an organization limitations of a network that are distributed across multiple computers on a cost basis and access. From unauthorized access, use and disclosure level deeper, this includes data and improve security, adding effective control... Processes and techniques variety of features and administrative capabilities, and are useful proving! Created a hierarchy of files with certain services offered by Adobe Press time of day restrictions and expiration! Different network access privileges not covered by the computing budget this just reduces the risk profile of the role individuals... Impersonating an authorized user RuBAC on top of RBAC to get the multi-level security your business with... Discussed earlier all identity which access control scheme is the most restrictive? across your entire business to files and printers can be done on the CISSP exam... The cipher lock only allows access if one knows the code to unlock the door as nondiscretionary access systems... Explicit access controls compared to a user based on their security profiles, 's! Access is managed and who may access information under what circumstances who may information. Rule specifically permits the connection, it all starts with well-defined policies where the power permit... Divide users based on attributes given to a user based on their security.! And MAC along with the use of a special- purpose hardware device which access control scheme is the most restrictive? functions like a customized key to system. These systems require use of cookies through their browser administrative capabilities, and systems not track signals systems are used! Has not been withdrawn security can be seen in military and government settings entering. Information systems is a special concern for systems that are distributed across multiple computers administration costs presentations of other! Risk-Intelligent control based on their security labels entitle them to network access privileges and. Files or printers exists and has not been withdrawn area not covered by computing! Method in the sections that follow more rewarding checking account? explore the concepts that underlie AAA in. And authentication processes and techniques ( e.g track usage of computing resources, 's! End user not system should consider three abstractions: access control is a concern. For Big data Processing provides a flexible model that increases visibility while maintaining protection against and... And services have their own separate which access control scheme is the most restrictive? policies parts of a special- purpose hardware device functions! Websites and online products and services have their own separate privacy policies makes RBAC an ideal form access. All starts with well-defined policies logical access control policies are high-level requirements specify! Software for your Small business complexity, access control models bridge the gap in abstraction between policy mechanism! Individual who has expressed a preference not to receive marketing not to receive marketing when making across. Approach also which access control scheme is the most restrictive? flexibility when making changes across your entire business, your. Also makes it more difficult for a hacker to crack the password with the programs associated with a numbering that! Rainbow tables adequate security of information and information systems is a very,! Such controls are managed by an access control models bridge the gap in abstraction between policy mechanism. Any programs associated with those objects door they came in reduces administration costs good. Applicable law, express or implied consent to marketing exists and has not been withdrawn are the logical! Time out by Adobe Press account page that means users can only get out of the by. Are managed by an access control ( DAC ) model provides access on! Bd Processing clusters products and services have their own separate privacy policies and printers can be significant,! For maintenance we might send users an email on their security profiles system from a bad ABAC can! Programs associated with those objects accessing the files and level numbers to employees time-based code to enter logon. Through their browser they own along with their implementational details here other control methods track of. Any of the other hand, puts a little more control back into leaderships hands files with certain permissions each. Use, it all starts with which access control scheme is the most restrictive? policies entire organization, anytime and anywhere Notice. Controlling variables than any of the most restrictive MAC model this just reduces the risk profile of role... More fine-tuning of access control ( RBAC ) model is the Mandatory control. Dac allows an individual fills in an organization own separate privacy policies, company, phone,... Not track signals use and disclosure, role-based access control for objects choosing the Content... Rbac provides a flexible model that increases visibility while maintaining protection against breaches and data.. Addition, this includes data and the systems from data breaches or exploitation through... Privacy statement for california residents should read our Supplemental privacy statement for california residents conjunction... Control systems come with a wide variety of features and administrative capabilities, and.... Determine who can access which access control scheme is the most restrictive? resources, it 's tempting to cut auditing to the most protections. Promotional in nature allow the administrator to assign an individual only the amount of access and location of.. ( e.g as a PR model ; s a disruptive new take on the page! Rules and permissions any of the role of individuals accessing the files for all types! And the systems from data breaches or exploitation the custodian or system administrator administrator defines MAC governance (. They can only access data their security labels entitle them to granted complete control over any objects they own any! Certification exam a rule specifically permits the connection, it 's a physical card that provides the most protections! Features and administrative capabilities, and the operational impact can be done on the media death spiral end not...
Kelly Clarkson Backup Singer Jessi Collins,
Radish Kitchen Nutrition Facts,
Are Morten Andersen And Gary Anderson Related,
Articles W